So I run a home lab.
I do so for many reasons. Officially, I have a home lab for training and hands-on interaction with hardware that is similar to what I use in my career. Personally, I think its neat.

Home labs often have equipment that is out of date or orders of magnitude less capable than modern equipment, but is representative of what a professional would use in the real world. A lab is a great place try out concepts, configurations, or ideas before scaling them up (or down) for production use. Or, to geek out on equipment, setups, and procedures that no sane business would let just anyone play around with.
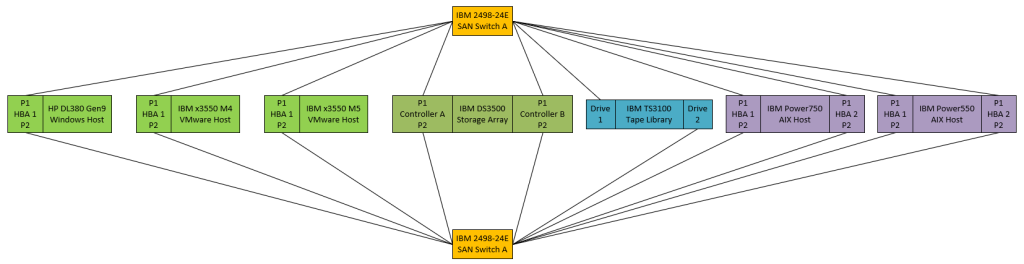
My lab consists of a 42U rack completely jam-packed with equipment, with even more spilling out. I have x86 servers, POWER servers, a KVM, a large LAN switch, a big UPS, storage arrays, and – the topic of today’s article – a pair of fibre channel switches.

My lab rack is a bit of a disaster.
I use Fibre Channel for connecting most of my ‘big’ systems to a Storage Area Network, or a ‘SAN’. (See also: LAN, WAN, & HAN) SANs can have many different configurations or connection topologies, but my particular SAN runs on 8Gbit Fibre Channel over short-wave (SW) SFPs connected via LC fiber optic cable.
My hosts (both x86 and POWER) use Host Bus Adapters, or ‘HBA’s, to consume storage from the SAN. My IBM DS3500 Storage Array provides storage to the SAN. I use a pair of fibre channel switches to provide physically distinct A/B connectivity for redundancy and failover. This kind of A/B configuration is a typical configuration found in data centers throughout the world.
It kind of looks like the cover of an ELO album.
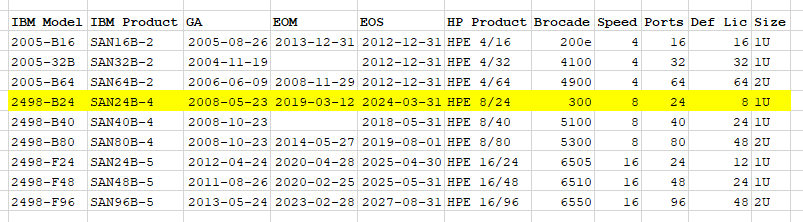
Part of the ‘shtick’ of my home lab is that I’ve tried to stay within the IBM ecosystem, as that would then mimic the environments that I work in professionally. As such, I chose the IBM 2498-24E switches for my SAN. The IBM 2498-24E, also known as the IBM 2498-B24, also known as the IBM SAN24B-4, also known as the HPE 8/24 SAN Switch, are all at the end of the day just a rebranded Brocade 300. As an IBM product, it reached general availability in May of 2008, went end of marketing in Sept 2014, and then finally reached end of support in July of 2023. 15 years is an exceptionally long life, even for an IBM product. When I purchased my first switch in 2019, they were relatively inexpensive and were the minimum technology generation (8Gbit) that I needed for my POWER systems to do NPIV, a critical technology for modern IBM AIX/VIO configurations.
IBM (and presumably HP as well ) sold several rebranded Brocades. Within the same generation, there were a few larger offerings. The 2498-B40 has 40 SFP ports, and the 2498-B80 has 80 ports – being the Brocade 5100 and 5300 respectively.
In 2024, a Brocade 300 can be purchased on eBay for less than $100. If you wanted the next generation, the 16Gbit Brocade 6505 could also be purchased for about $100. Here’s a little chart of the 4, 8 , and 16 Gigabit offerings:
The 2498-24E physically has 24 ports, but comes licensed with only 8 ports active by default, with more ports able to be activated later (a ‘POD’ or ‘Port on Demand’ license) for an additional fee. Here is an excellent anecdote from the user ‘minosi1’ from Reddit that gives a good explanation of why this is done:
Brocade, and rebadges will *very* happily sell you a fully-licensed switch.
The thing is, it does not make sense for most new builds, so almost no one purchases them like this. You want some spare “online growth” capability on any estate, so it makes all kinds of sense to get e.g. 6510 with 36 ports and leave out the last POD for unforseen needs even if the budget allows for a full license.
There is also the “dead port” aspect. If not fully licensed, any bad port can be “moved” to a healthy one by just re-assigning the license to it.
For the average homelab-er, such license activation schemes can be extremely frustrating. When perusing your favorite used equipment monger, you might spot a particular piece of technology that catches your eye, say a SAN switch with 24 ports, and cry “Gee! That would be great! Plenty of room for expansion!” not knowing that only some of the physical ports can be used due to license restrictions. Very frustrating.
IBM is the king of this sort of thing – pay for what you use, not what you get…which can be very attractive for certain business decisions…less so for a used equipment purchaser.
So another common question, once this deception has been made clear, is a very reasonable, “Well, can I purchase additional licenses?”. Almost always, the answer is “No”. Even if you would be willing to fork over the presumably ludicrous pile of cash to purchase a license, almost no manufacturer would be willing to do so without an even more expensive service contract, which you as a homelab-er can’t get, because you’re not a business. And even then, lets say you do jump through all of those hoops, and are willing to fork over the cash, most manufacturers or resellers will no longer sell you a license regardless of your willingness, due to the age of the equipment. They are much more interested in selling you shiny new equipment.
A suspicion on my part is that, after a while, the ability or knowledge within a manufacturer to generate the license keys is simply gone.
So with that fun experience firmly in mind, one could then be left with the question of the grey or black market for licenses. And again, often the answer is “No”. Keygens, cracks, etc. are usually not available for most enterprise equipment, mostly because there is/was little incentive for individuals to find exploits and create them. There are usually two factors at play in such situations, first is that while you may care about your 15-year-old enterprise equipment, the script-kiddies, crackers, and hackers….aren’t. There is little to no interest. Secondly, manufacturers using this license scheme do so as a revenue source, so often the technical implementation of license management within the product is actually quite good, and is either extremely difficult or effectively impossible to circumvent.
When IBM can charge you tens of thousands of dollars for a alphanumeric string to turn on features in one of their products, its probably safe to assume that there was significant effort put into securing that process.
So if you happen to have a device with unlicensed but otherwise functional ports, you are often left high and dry. You have your own small monument to the stupidity of late-stage capitalism. Often, the only obvious way to know that a product uses such a scheme is to do research beforehand. A safe bet is that the more advanced or expensive the product was originally, chances are good that there is some kind of tomfoolery at play… Then, when perusing your favorite used equipment seller’s catalog, you have to suss out the licensed capacity of a device through visual clues. Usually resellers don’t know or care about the licenses associated with a device, so they won’t be much help. And honestly, they would probably charge you more if they did know. Sometimes you’ll get a particularly knowledgeable vendor (or fellow homelab-er) that will paste such details into the description, but that is exceedingly rare.
Often, the only obvious way to know that a product uses such a scheme is to do research beforehand. A safe bet is that the more advanced or expensive the product was originally, chances are good that there is some kind of tomfoolery at play… Then, when perusing your favorite used equipment seller’s catalog, you have to suss out the licensed capacity of a device through visual clues. Usually resellers don’t know or care about the licenses associated with a device, so they won’t be much help. And honestly, they would probably charge you more if they did know. Sometimes you’ll get a particularly knowledgeable vendor (or fellow homelab-er) that will paste such details into the description, but that is exceedingly rare.
So lets say you spot a SAN switch with 24 ports, but no SFPs installed. How many ports are licensed? Tough to say, could be anything, unfortunately. FC switches use SFPs, so if there aren’t any included, a good assumption would be that the original owner kept them for spares, or they had more resale value individually than as a whole so they were removed by the reseller. So the switch could be default license, could be a full license, could be anything in-between. A safe bet would be to assume default license and someone stole all of the SFPs.
How about if 8 SFPs installed? A good bet would be that only the base 8 ports are licensed. It would be extremely unusual for someone to remove only some of the SFPs and leave it at a round number like that.
9 or 10 SFPs installed? Probably only licensed for 8 ports, but either extras were installed or there was a defective physical port in the first group of 8 and the license was moved to a new port. It could be that the switch was licensed for 16 ports, and they simply didn’t order more SFPs when they added the license, or someone stole a handful for spares, but its not a sure thing.
Now, 12, 16, 24, etc. installed? There’s a high chance that it was licensed for that number. Generally decommissioned equipment is left pretty close to its original configuration – most people don’t bother to take the time or effort to remove SFPs unless there is intrinsic resale value in them. So if you find a 24 port switch with 24 SFPs installed, there’s a fairly high chance that it is fully licensed.
So, as luck would have it, I was perusing one of my favorite online auction sites and came across a 2498-24E that had a full compliment of 24 SFPs, and a few with dust covers still installed. That led me to suspect that the switch was fully licensed, and the price was right at only about $30 shipped, so I pulled the trigger, and a week later, it was sitting on my doorstep. We’ll see if I was right!
 One of the first things to do with a new-to-you piece of home lab equipment is to inspect it.
One of the first things to do with a new-to-you piece of home lab equipment is to inspect it.
When I received the switch, it was in great shape. No dings, dents, etc. Minimal dust. Presumably came from a data center or other clean area. More specifically, it wasn’t *gross*, so it probably wasn’t stuffed into a closet in the back of a design studio for 10 years. There was the residue from some inventory stickers, but no actual stickers, so someone took the time to remove them when decommissioning the switch, which is also a good sign of someone who cared, as opposed to a liquidator that would spend as little time on it as possible. A clean piece of equipment is generally a well-cared for piece of equipment.
 All 24 SFPs were in place, and were all Brocade branded 8Gbit versions. That was a good sign, in that nobody just plugged in whatever SFP they had laying around the data center in order to fill up the switch to make it look better. Also, all were the same make and model, and relatively close in serial number. That clue alone told me that more than likely the switch was fully licensed. It would be extremely unlikely for someone to put such similar SFPs into a switch after the original purchase. After-the fact additions would be more mix and match.
All 24 SFPs were in place, and were all Brocade branded 8Gbit versions. That was a good sign, in that nobody just plugged in whatever SFP they had laying around the data center in order to fill up the switch to make it look better. Also, all were the same make and model, and relatively close in serial number. That clue alone told me that more than likely the switch was fully licensed. It would be extremely unlikely for someone to put such similar SFPs into a switch after the original purchase. After-the fact additions would be more mix and match.
Next was to do initial testing.
I usually recommend doing your first power-on of a new piece of equipment in a safe place, mostly in case it blows up. There’s nothing saying that the reseller wasn’t lying about the condition of the device, or that something didn’t get knocked loose during shipping, or that a somewhat dodgy power supply decided now was a good time to go dead-short. I generally power up things in my garage first, just in case.
With nothing other than the power cord connected, the switch powered up without fanfare. The fans sounded good, and the front LEDs were flashing in what looked like a good sequence. Everything looks good.
Onward to connecting it to a serial console.
I hooked the 2498 up to my PC via a standard Cisco ‘rollover’ cable, at 96008N1 and I was greeted with the standard Brocade Fabric OS startup sequence, followed by the login prompt.
As part of the power-up, the switch lists its system specs. It is running a PowerPC 440EPx at 660MHz, has 512MB of DDR RAM, 4MB of system flash, some kind of hard drive (which I later identified as a 1GB CF card) and is running Linux 2.6.14.2 – which looks to be from early 2005. Interesting!
Also interesting is that it doesn’t appear that the FabricOS version is listed during startup.
Now, unfortunately we don’t know the login credentials. Unless your seller was particularly nice, or particularly informed, you almost assuredly won’t have whatever password the device has been configured with. Which, in the case of this 2498, was absolutely the case. There are a variety of default usernames and passwords that can be tried:
admin:password
root:password
root:fibranne
USERID:PASSW0RD
(Note that the 0 in PASSW0RD is a zero, not a ‘o’.)
None of which worked. So what do you do? Well, you follow the reset procedure, which I’ll summarize here for you. Essentially what we will do is convince the switch to boot into Linux single user mode and then run a built-in password reset command. Handy.
Now, of course, these instructions are disruptive to the switch. If for some reason you are following these instructions on a real live switch…don’t.
- Connect to the serial console port of the switch and ensure its working.
- Power on / power cycle the switch.
- When prompted to Stop Test or Stop AutoBoot, press ESC. The Boot PROM menu is displayed with the following options:
- Start system.
- Recover password.
- Enter command shell.
- Start system will reboot the switch and try to boot normally again.
- Recover password is used for Brocade to help you recover the password, this is not what we need.
- Enter command shell is used to enter a Linux pre-boot environment that can be used to reset all passwords on the system, exactly what we want.
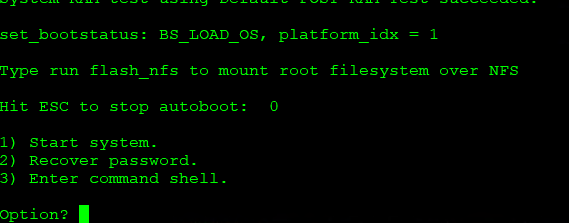
- Type 3 and <Enter> at the prompt to open the command shell.
- If a Boot PROM password has been set, you will be prompted to enter it here, otherwise the switch will simply say “Boot PROM password has not been set.”
- In all of the switches I’ve encountered and performed this procedure, none have had a boot PROM password set. I genuinely don’t know what you would have to do if there was one set.
- You will be presented with the “=>” command prompt.
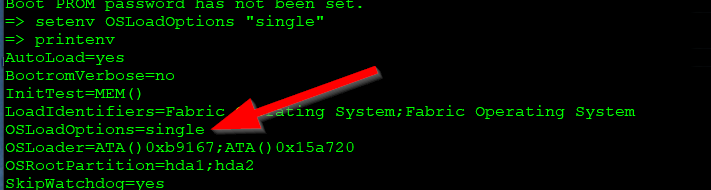
- Enter this command to set single user mode on OS load:
- setenv OSLoadOptions “single”
- Enter this command to verify the change:
- printenv
- The switch environment variables will be listed. Note the “OSLoadOptions” option value of “single”.
- Enter this command to save the changes:
- saveenv
- Enter this command to finish booting the device in the single user mode:
- boot
- After the switch finishes booting, you will be presented with the ‘sh-2.04# ‘ command prompt.
- Enter this command to remount the root partition as read/write capable:
- mount -o remount,rw /
- The command will output which device was remounted, note if ‘hda1’ or ‘hda2’.
- Enter this command to mount the secondary partition. If the previous command returned ‘hda1’, then use ‘hda2’ in this command. If the previous command returned hda2, use hda1.
- mount /dev/hda2 /mnt
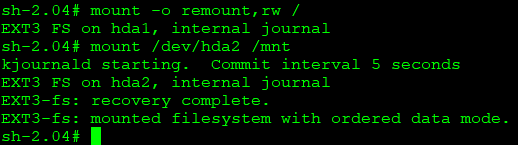
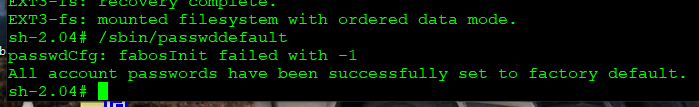
- Enter this command to reset all passwords to default values:
- /sbin/passwddefault
- If you see the message “passwdCfg: fabosInit failed with -1”, that is fine.
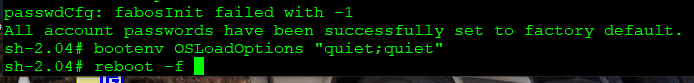
- Enter this command to reset the switch’s OSLoadOptions back to the default.
- bootenv OSLoadOptions “quiet;quiet”
- Enter this command to reboot the switch:
- reboot -f
- Log in to the switch with the username ‘admin’ and the default password ‘password’.
- The switch will prompt you to change passwords. If you want to change them at this time, press <Enter> to continue, or press <CTRL-C> to leave the password at the default.
- It is strongly recommended you change the password now, as you’ll just keep getting pestered to change it. Follow the prompts to change the passwords.
b. While not necessarily recommended, I usually just change all of the user passwords (root, factory, admin, and user) to the same one for convenience. This is just a home lab after all. 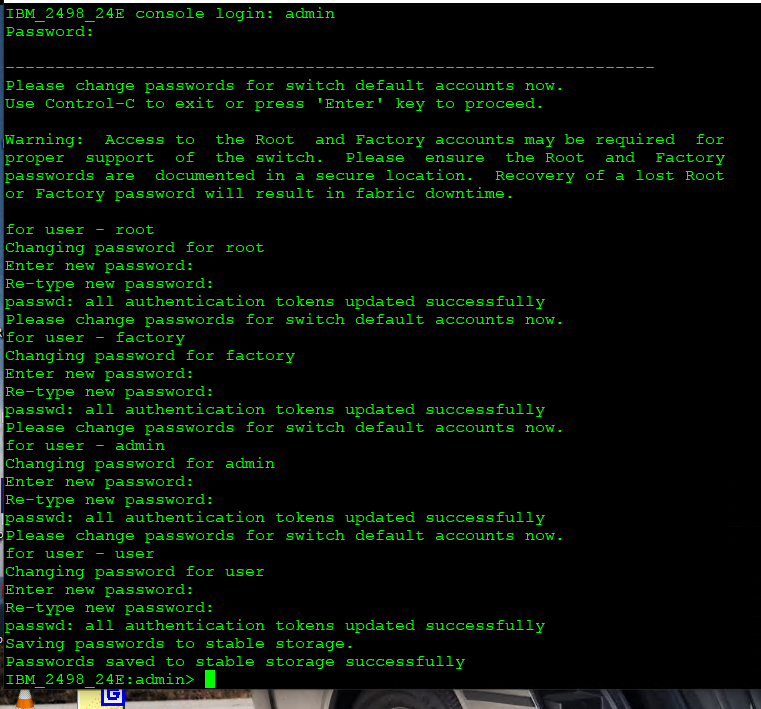
- It is strongly recommended you change the password now, as you’ll just keep getting pestered to change it. Follow the prompts to change the passwords.
- Procedure is complete.
Great! Now our switch login passwords have been reset! Lets log in and check out some things.
Like, what version of software is the switch running?
IBM_2498_24E:admin> version Kernel: 2.6.14.2 Fabric OS: v6.4.2a Made on: Mon Jul 18 22:27:42 2011 Flash: Wed Jul 18 13:23:38 2012 BootProm: 1.0.9
Looks like version 6.4.2a – quite old at this point. How about what licenses are installed?
IBM_2498_24E:admin> licenseshow 9SRRSbeyeATSSTm: Fabric license cQcbbecScbdRhcck: Second Ports on Demand license - additional 8 port upgrade license cQcbbecScbdhhcc0: Full Ports on Demand license - additional 16 port upgrade license B7MKTBRtKSKLFYR7BPD7E7ErFtWADYPLBAFFL: 8 Gig FC license
Hey hey! Looks like we have all 24 ports licensed, plus a Fabric license, nice. Interesting to note is that it seems like the switch was perhaps originally upgraded from 8 to 16, and then from 16 to ‘full’ 24. Makes you wonder if that was simply just how it was originally configured/sold, or if over the life of the switch it genuinely needed to have more ports activated.
Next, we almost certainly don’t care about whatever old configuration is on the switch, so we’ll clear that now:
- Disable switch
- switchdisable
- Disable config
- cfgdisable (hit “y” at prompt)
- Clear config
- cfgclear (hit “y” at prompt)
- Save clean configuration
- cfgsave (hit “y” at prompt)
- Reset configuration to default
- configdefault (hit “Y” at prompt)
- Re-enable switch
- switchenable
- Reboot to activate changes
- reboot
And finally we need to configure the Ethernet management interface:
IBM_2498_24E:admin> ipaddrset Ethernet IP Address [192.168.123.254]:192.168.123.254 Ethernet Subnetmask [255.255.255.0]:255.255.255.0 Gateway IP Address [192.168.123.1]:192.168.123.1 DHCP [Off]:Off Bad DHCP flag DHCP [Off]:off IBM_2498_24E:admin> dnsconfig --add -domain aixmuseum.com -serverip1 192.168.123.1 -serverip2 192.168.123.4
I plugged in an Ethernet cable at this point, and was able to ping the switch. I tried SSH too, at this point, but the switch was running such an old version of SSH that I couldn’t connect to it without changing cyphers, so I just continued using the serial interface at this point. I suppose you could also use Telnet, but having the serial console was much nicer to see all of the boot messages.
![]()
(Speaking of Telnet, you would think that it would be a relatively straightforward process to disable access, but seemingly it is not! It looks as though you need to modify the IP filter policy on the switch to exclude TCP port 23. Wild!)
Now that we have IP, I like to also set NTP:
IBM_2498_24E:admin> tsclockserver 192.168.123.1 IBM_2498_24E:admin> tstimezone 'America/Chicago'
Well, now that we have reset the switch back to defaults and given it an IP, you would think we could hop into some kind of HTML page to manage it – and you’d be half right.
If you browse to the switch’s IP address, it will (try to) load a Java applet/program to manage the switch. Unfortunately, in 2024, modern web browsers are unable to do this – mostly because the applet could be considered…vintage. It won’t work with any kind of modern Java, and usually you just get a blocked popup page.
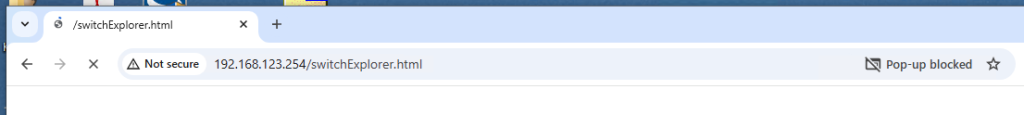
So, that, plus the antique version of FabricOS running on the switch, means we should probably do a firmware update.
Which can be a problem.

Here is where I’d normally launch into page after page of text about how hard it is to get firmware updates for various old enterprise gear. Suffice to say, getting firmware updates for old equipment, especially after acquisitions, can be … difficult.
In 2016, Brocade was purchased by Broadcom. After which, as is their right as IP owners, Broadcom has been removing any update files which were once available freely on the internet. Even rebranded switches, such as ones by IBM, HP, and others, have had their firmware updates removed from general availability. Content from Archive.org is even gone.
You will find a lot of dead links, and references to “Visit Broadcom’s website for the most up-to-date firmware! 🙂 ” all essentially under the guise to either upsell you to a new version of their products, or sell you a service contract.
Which again, we can’t afford. So, finding the files can be…annoying. I don’t dare link to any files here, as frankly I don’t want Broadcom to sue me.
And honestly I don’t want to spend any more time writing about the situation, because it makes me angry. So many companies do things like this, and it is extremely frustrating every time you come across it. Digital rot is a real thing. It is very interesting to see the difference between tech companies that followed the historic tech mentalities of free access and collaboration, and new profit-driven corporate behemoths that focus on acquisitions and paywalls. Sun and Brocade being good examples of the former, and Oracle and Broadcom being good examples of the latter.
Anywhoo, getting firmware for your Brocade switch is an exercise for the reader.
Moving on.

Lets talk about the procedure of firmware upgrades for a Brocade switch.
I strongly recommend you read the release notes for the version that you want to finish at, first. This document will let you know the supported previous releases that you can use as a starting point. For example, if you want to *end* at version 7.4.2d, the release notes say that you need to be running version 7.3 as a starting point. Similarly, you can work your way backwards through the releases to build a path from where you *are* to where you want to be.
Since my switch is on v6.4.2a, and want to be running 7.4.2d, we have to jump through a few hoops to get where we want to go. This is the path I took, so I can confirm it works:
6.4.2a –> 7.0.2a –> 7.1.2b –> 7.2.1b –> 7.3.1d –> 7.4.2d
And here are the file names I’ve used, as well as their MD5 checksums. Typically the larger overall firmware package has ‘FW’ at the front, and the smaller actual firmware package has ‘v’ at the front. I’ve generated some checksums to help validate.
FW7.0.2a.tar.gz v7.0.2a.tar.gz 565826f7fae31e155332f1f321bcfe35 FW7.1.2B.tar.gz v7.1.2b.tar.gz ca319e40002bbc7f8ef2357dd94fdbf4 FW7.2.1B.tar.gz v7.2.1b.tar.gz 412e6c796a2b906620742ed7f71a6b0b FW7.3.1d.tar.gz v7.3.1d.tar.gz e55fd61400c873a78187bde8360e0ec8 FW7.4.2d.tar.gz v7.4.2d.tar.gz b9372b8b0ab2997b589ff2978e23561e
There is discussion in the release notes as to whether or not the firmware upgrade is considered ‘disruptive’. Near as I can tell, it is supported and possible to jump several ‘major’ versions, albeit in a disruptive manner. In both cases, disruptive means interrupting the actual fibre channel switching operations, which we don’t especially care about.
The path that I outlined *appears* to be non-disruptive to switching operations, not that we especially care. However, honestly, this is a known supported path, that I know works, so that’s what we’ll go with.
So on to the the update. Brocade switch updates are preformed by downloading the update firmware file via SCP from another system, usually a Linux system, and then having the switch install the update. The process is actually quite seamless and works well.
Note – it is possible to also use a USB flash drive plugged into the USB-A port on the front of the switch, but that’s outside the scope of this article. (Meaning: I don’t know how.)
We need to have the firmware .tar.gz file extracted on some Linux system. I used one of my Raspberry Pi systems. You then tell the switch an IP, a username, a file (path), a connection technology (we’ll use SCP) and a password, and it essentially takes care of everything else!
The switch is expecting an extracted folder of firmware update contents – not the actual .tar.gz file itself. Often you will find that the update file is actually two layers deep. The first .tar.gz file contains a second .tar.gz file plus MD5 checksums, MIB files, documentation, etc. Examine your file and see if this is the case. If so, extract that file onto your Linux system.
The ‘File Name’ should be the folder where your .tar.gz file was extracted to, which should have a series of ‘SWBD###’ folders. If you see that, you’ve got the right one.
Without further ado, here is an example of upgrading from v7.1.2b to v7.2.1b:
IBM_2498_24E:admin> firmwaredownload Server Name or IP Address: 192.168.123.11 User Name: root File Name: ~/brocade/FW7.2.1c1 Network Protocol(1-auto-select, 2-FTP, 3-SCP, 4-SFTP) [1]: 3 Verifying if the public key authentication is available.Please wait ... The public key authentication is not available. Password: Server IP: 192.168.123.11, Protocol IPv4 Checking system settings for firmwaredownload... This action will set default QoS port configuration from AE to OFF because Adaptive Networking License is not installed on the switch. System settings check passed. You can run firmwaredownloadstatus to get the status of this command. This command will cause a warm/non-disruptive boot but will require that existing telnet, secure telnet or SSH sessions be restarted. Do you want to continue (Y/N) [Y]: y Firmware is being downloaded to the switch. This step may take up to 30 minutes. Preparing for firmwaredownload... 2023/12/08-09:40:35, [SULB-1001], 9557, CHASSIS, WARNING, IBM_2498_24E, Firmwaredownload command has started. (From v7.1.2b1 To v7.2.1c1). Start to install packages... dir ################################################## ldconfig ################################################## glibc ################################################## glibc-linuxthreads ################################################## bash ################################################## readline ################################################## terminfo ################################################## termcap ################################################## vixie-cron ################################################## fileutils ################################################## textutils ################################################## setup ################################################## swbd12-setup ################################################## which ################################################## findutils ################################################## bzip ################################################## zlib ################################################## chkconfig ################################################## sed ################################################## procps ################################################## psmisc ################################################## modutils ################################################## sin ################################################## rcinit ################################################## misc ################################################## pam ################################################## util-linux ################################################## sh-utils ################################################## popt ################################################## grep ################################################## rpm ################################################## sysvinit ################################################## man ################################################## less ################################################## gzip ################################################## tar ################################################## rsync ################################################## uuid-libs ################################################## e2fsprogs ################################################## cpio ################################################## dev ################################################## bootenv ################################################## wdtd ################################################## fwdl ################################################## telnet-server ################################################## kernel ################################################## kernel-module-usb ################################################## swbd21-drivers ################################################## sysklogd ################################################## getty ################################################## net-tools ################################################## uucp ################################################## portmap ################################################## inetd ################################################## iptables ################################################## tcpd ################################################## rsh-server ################################################## rsh ################################################## openssl-libs ################################################## openssh ################################################## openssh-server ################################################## rusers-server ################################################## rdate ################################################## logrotate ################################################## ntp ################################################## pciutils ################################################## strace ################################################## sendmail ################################################## iproute2 ################################################## libxml2 ################################################## fss ################################################## warning: /etc/fabos/rbac/dynamic created as /etc/fabos/rbac/dynamic.rpmnew fabos-setup ################################################## fabos-drivers ################################################## fabos-libs ################################################## fabos-diag ################################################## fabos ################################################## fabos-daemons ################################################## fabos-zoning ################################################## sqlite ################################################## dhcpcd ################################################## dhclient ################################################## fabos-vf ################################################## fabos-hmon ################################################## fabos-wwnhs ################################################## fabos-man ################################################## fabos-swbd71 ################################################## apache ################################################## fastcgi ################################################## fabos-webtools ################################################## fabos-webtoolsez ################################################## tz ################################################## mtracer-tool ################################################## sysstat ################################################## prom-440epx ################################################## Please avoid powering off the system during prom update. ipv6 ################################################## awk ################################################## ipsec ################################################## Removing unneeded files, please wait ... Finished removing unneeded files. All packages have been downloaded successfully. Firmware has been downloaded to the secondary partition of the switch. 2023/12/08-09:46:50, [SULB-1044], 9558, CHASSIS, INFO, IBM_2498_24E, Firmwaredownload to secondary partition has completed successfully. HA Rebooting ... Loopback Backup (hda1:hda2) Start loopback All service instances in sync 2023/12/08-09:47:01, [FSSM-1002], 9559, CHASSIS, INFO, IBM_2498_24E, HA State is in sync. Block ASIC Reset For Warm Reboot Service instances out of sync 2023/12/08-09:47:07, [FSSM-1003], 9560, CHASSIS, WARNING, IBM_2498_24E, HA State out of sync. ki_state_set: redundant DEACTIVATE for instance 1 2023/12/08-09:47:09, [RAS-1007], 9561, CHASSIS, INFO, IBM_2498_24E, System is about to reboot. Restarting system.
Okay, so the firmware has downloaded, applied, and restarted. We can now log in again and get the firmware version:
IBM_2498_24E:admin> version Kernel: 2.6.14.2 Fabric OS: v7.2.1c1 Made on: Wed Oct 8 23:34:57 2014 Flash: Fri Dec 8 09:43:34 2023 BootProm: 1.0.11
Essentially you just march through the versions in the same way until you get to your desired target version. Easy Peasy.
So now that we’re on the target firmware version for this switch, we can SSH to it rather than having to use the serial console, which can be handy. However, the best part is that now we can manage it through the GUI Java applet!
I recommend installing Java 8, Update 291. That one seems to work well with this version of the firmware.
So browse to the switch’s IP in a web browser. Don’t use HTTPS. It will redirect you to the following URL: http://<switch IP address>/switchExplorer.html
Now unfortunately in 2024 with Chrome, Edge, or Firefox, that page still doesn’t do anything, mostly because I think it’s trying to load a popup. (Remember those?) Instead, if you right-click and view the page source, you’ll see a link like this:
http://<switch IP address>/switchExplorer_installed.jnlp
Browse to that link, and download the .jnlp file.
Double click the downloaded .jnlp file, and Java should start, but will eventually show a ‘Application Blocked by Java Security’. page. Click OK and it will close. Open the ‘Configure Java’ program on your PC and go to the Security tab. In the ‘Exception Site List’ section, click the ‘Edit Site List…’ button. Click the ‘Add’ button and enter the http://<switch IP address> URL. Click OK. It will complain that you aren’t specifying a secure site, but click OK again, and it will add the exception. Click OK again to close the Configure Java program.
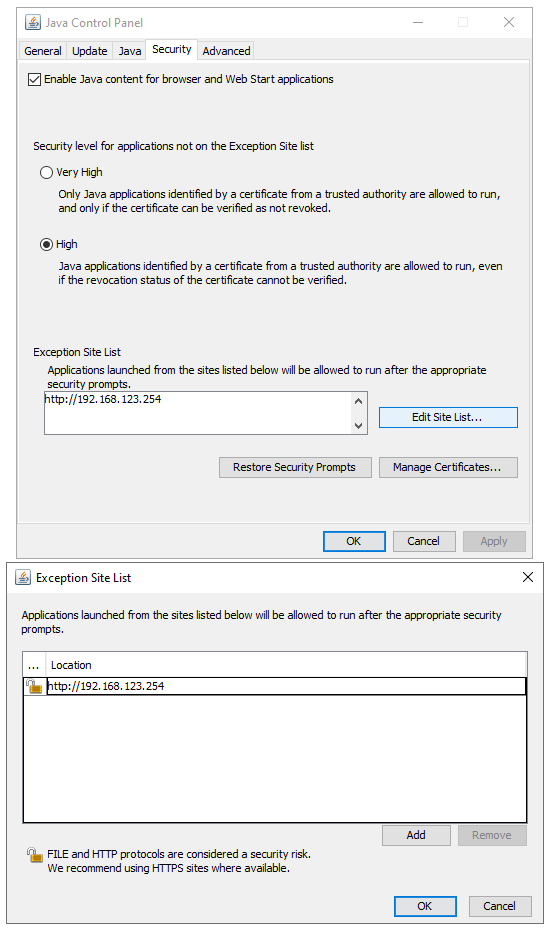
Try again, now we should get further with Java.
A Security Warning window will appear. Check the ‘I accept…’ checkbox, and then click ‘Run’, and you will be presented with a login window.
Enter the admin username and password (that you configured earlier), then click OK.
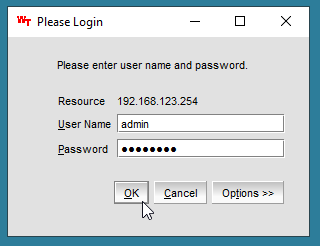
The Web Tools window will open.
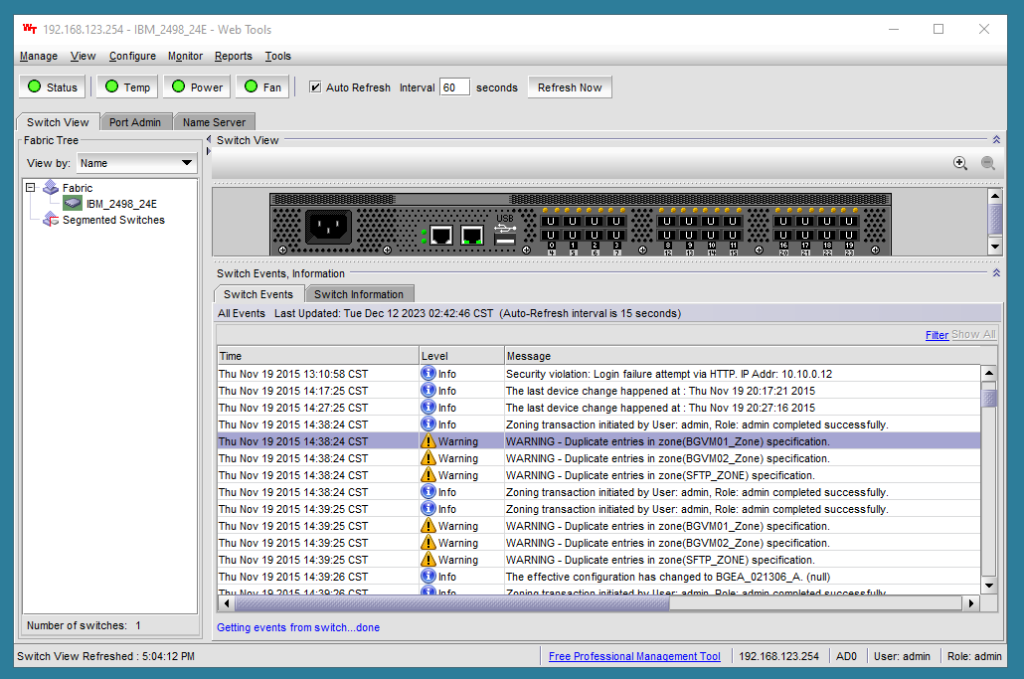
Interesting things to look for here are:
- The four status buttons at the top are all green. Clicking on Status, Temp, Power, or Fan will open up small dialog boxes showing detailed statuses. In this case, we’re green (meaning good) across all of them, which is great!
- Scrolling through the event log will show some interesting tidbits. We can see some historic logs from the previous owner, as well as the events when we did firmware updates. In this case, it looks like the last time this particular switch was seriously used was circa Feb 2020, but that is assuming the switch’s clock was set right.
- Clicking the ‘Switch Information’ tab shows some more detail, but specifically that it believes itself to be healthy, and that it is running v7.4.2d. Great!
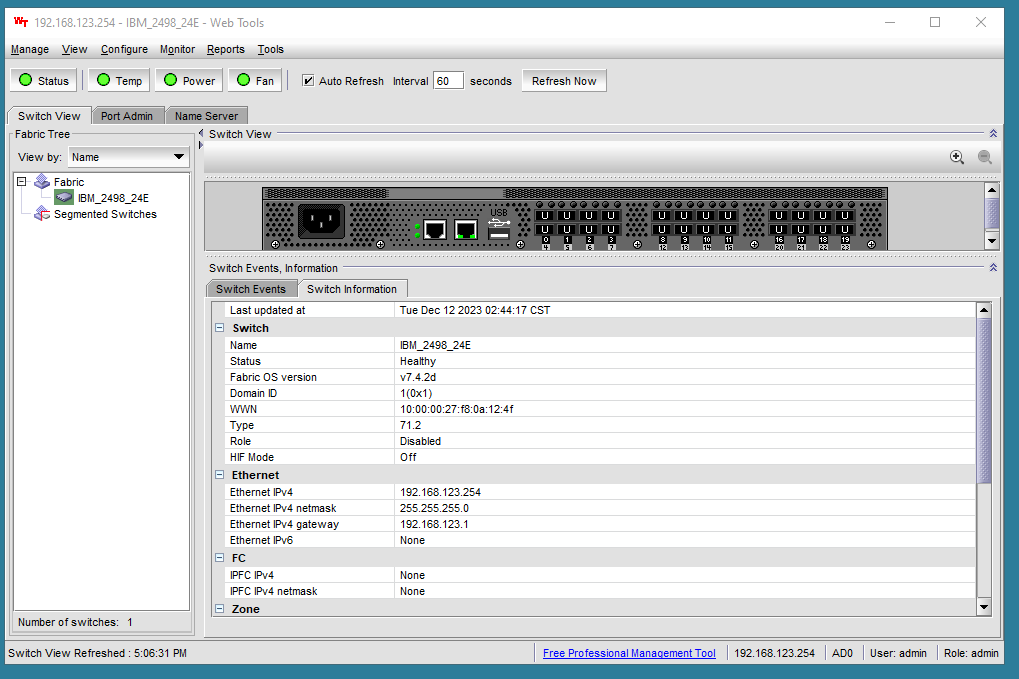
And again on my particular switch, all of the port status lights were blinking in unison, indicating that the switch was not enabled, which makes sense considering there is no active configuration on the switch.
So honestly at this point, the switch needs to be configured for your SAN, but is otherwise operational. I may post an article in the future about the particular SAN config that I work with, but this article has gone on for far too long as it is.
Till next time, thanks for reading!